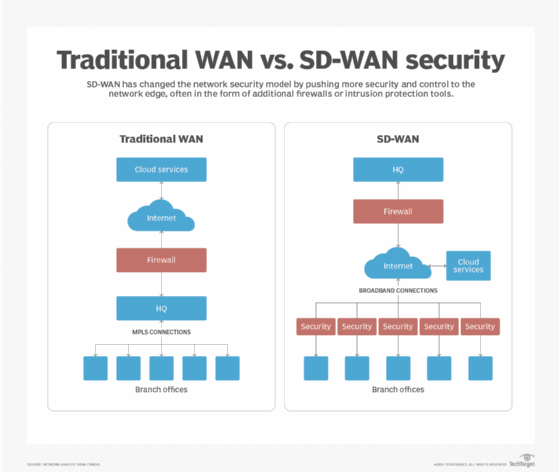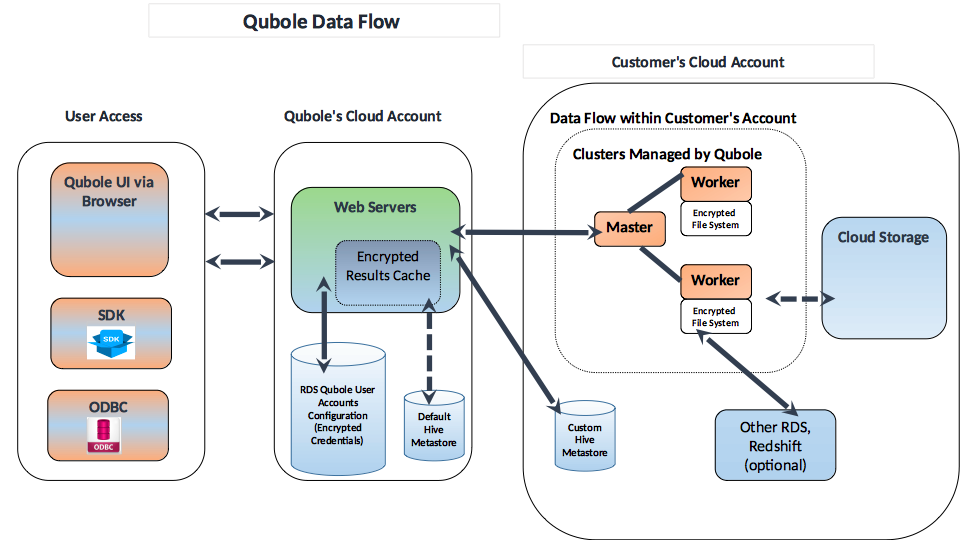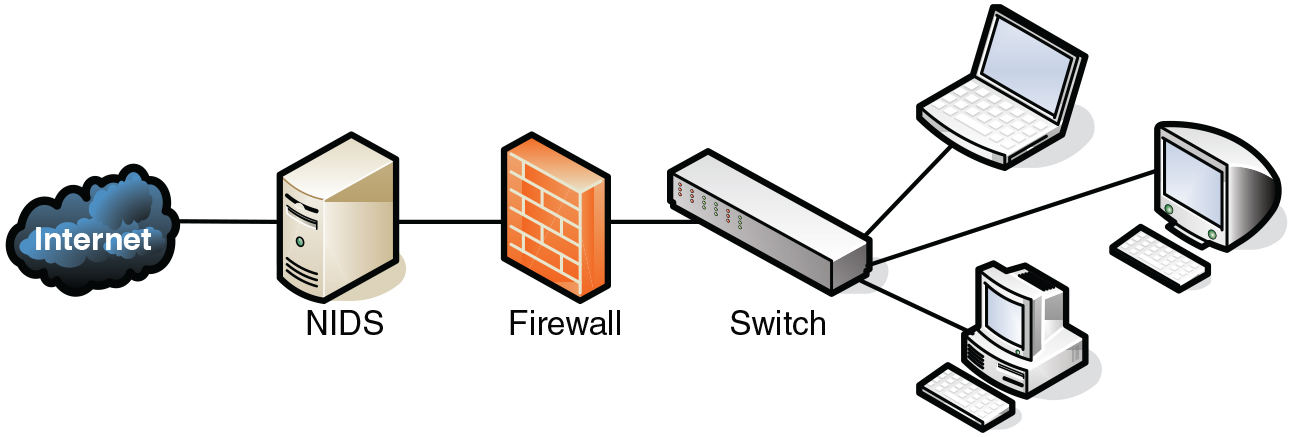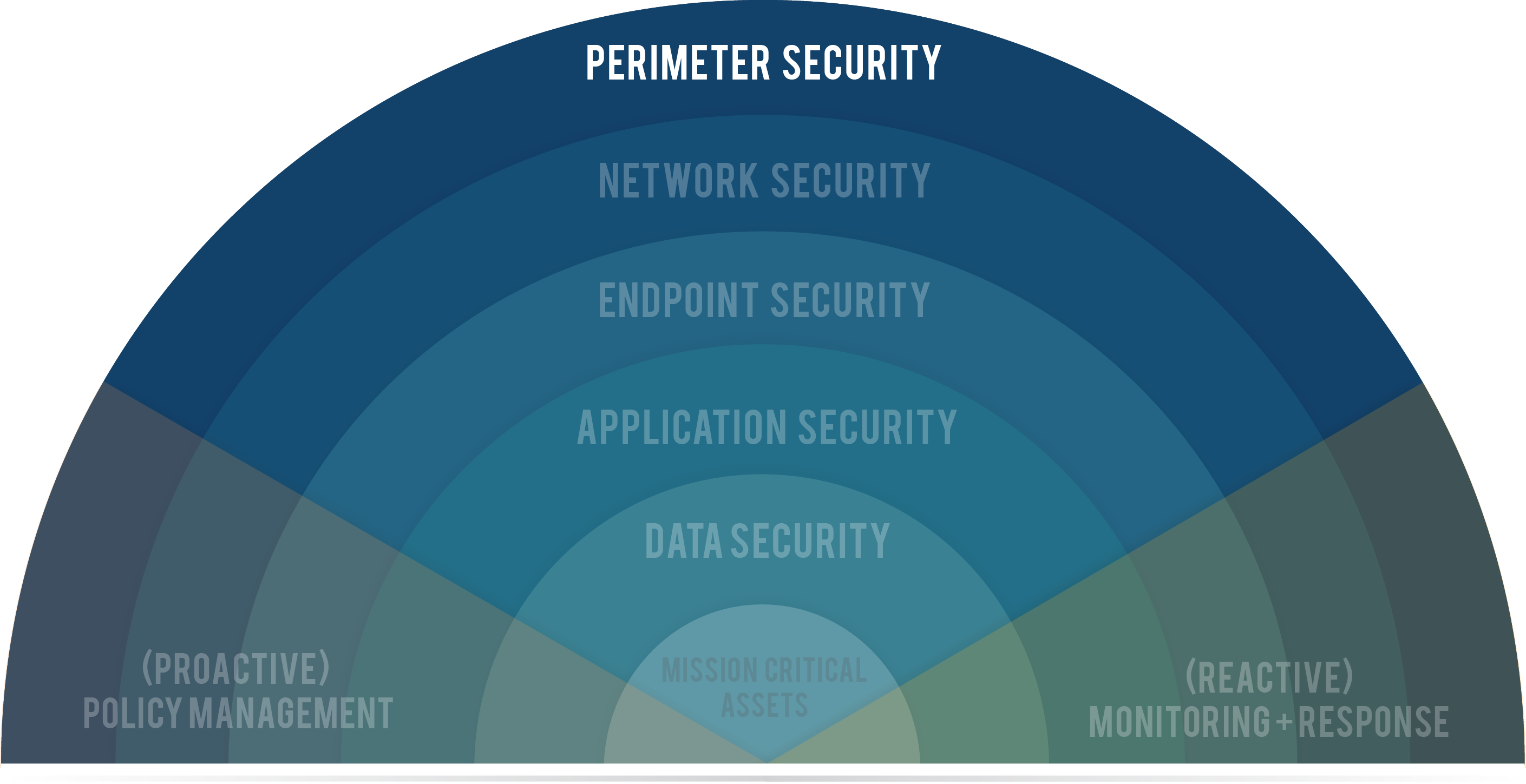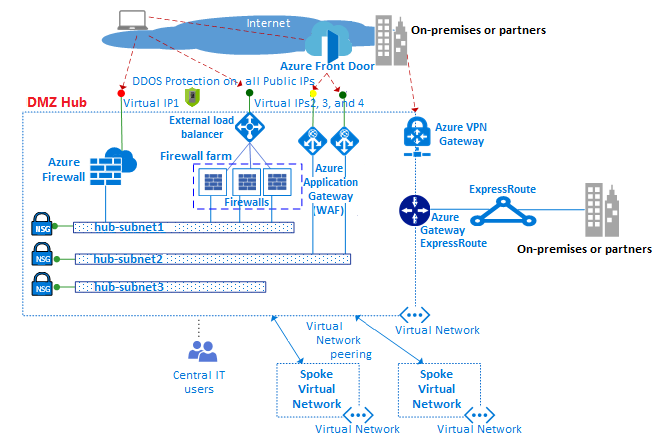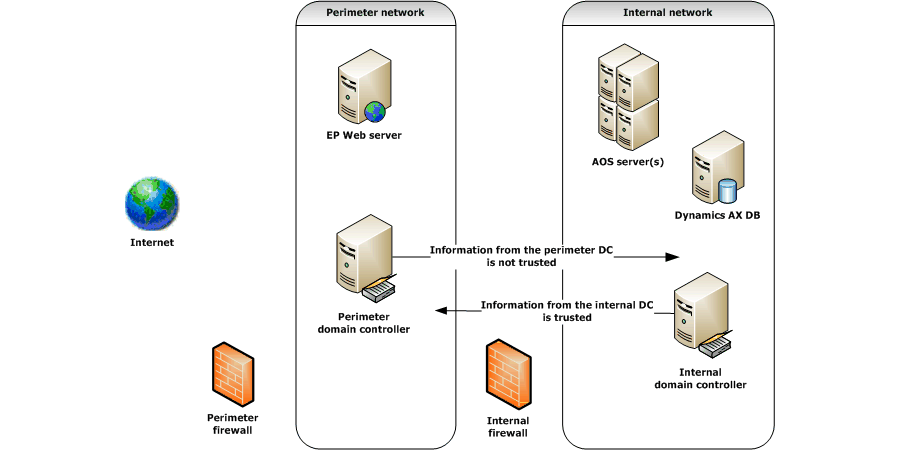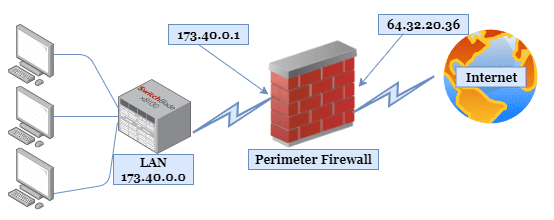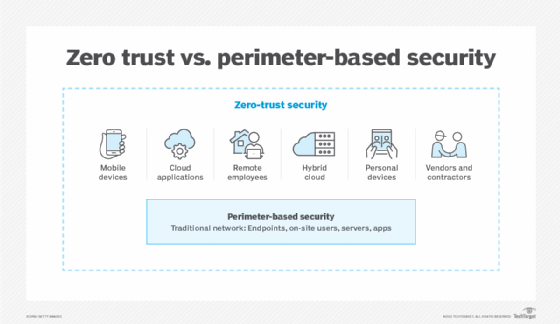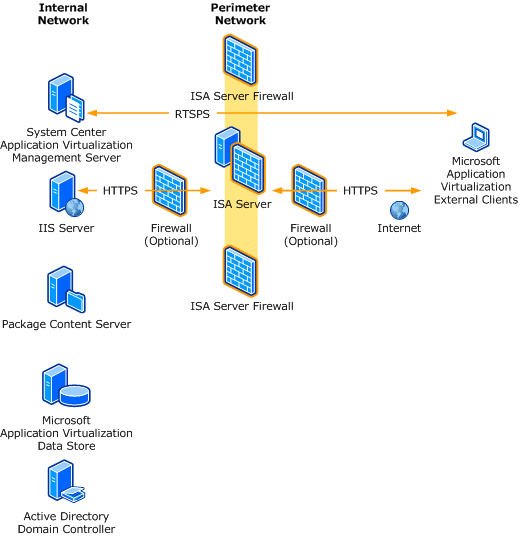
Internet-Facing Server Scenarios for Perimeter Networks - Microsoft Desktop Optimization Pack | Microsoft Learn
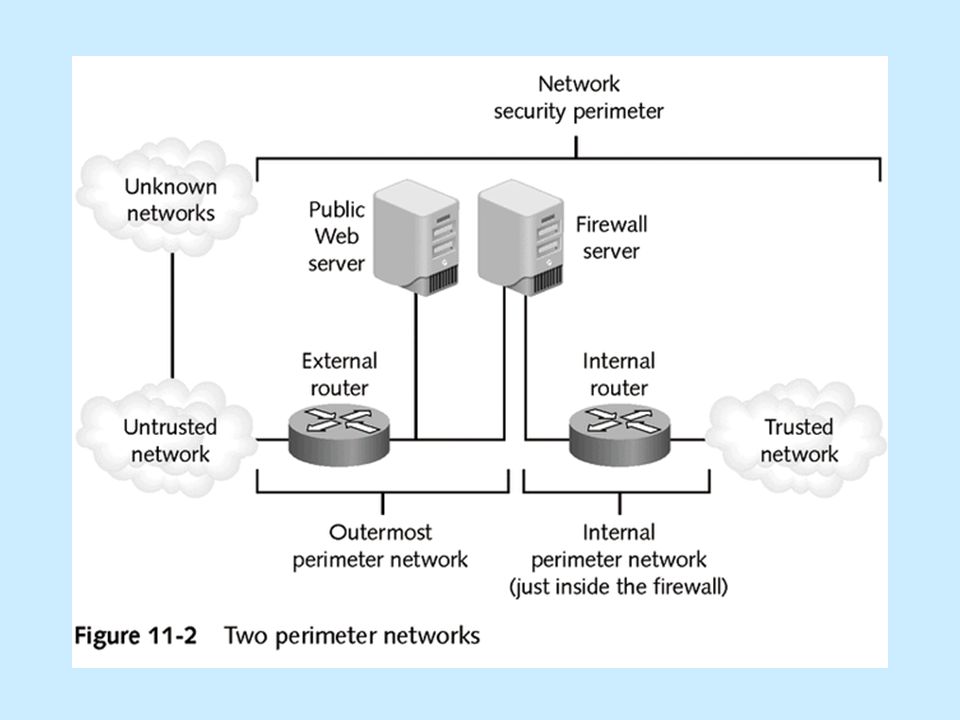
Network Security Topologies Chapter 11. Learning Objectives Explain network perimeter's importance to an organization's security policies Identify place. - ppt download
Network Configuration for Workgroup PDM Viewer in a Perimeter Network - 2012 - SOLIDWORKS Installation Help
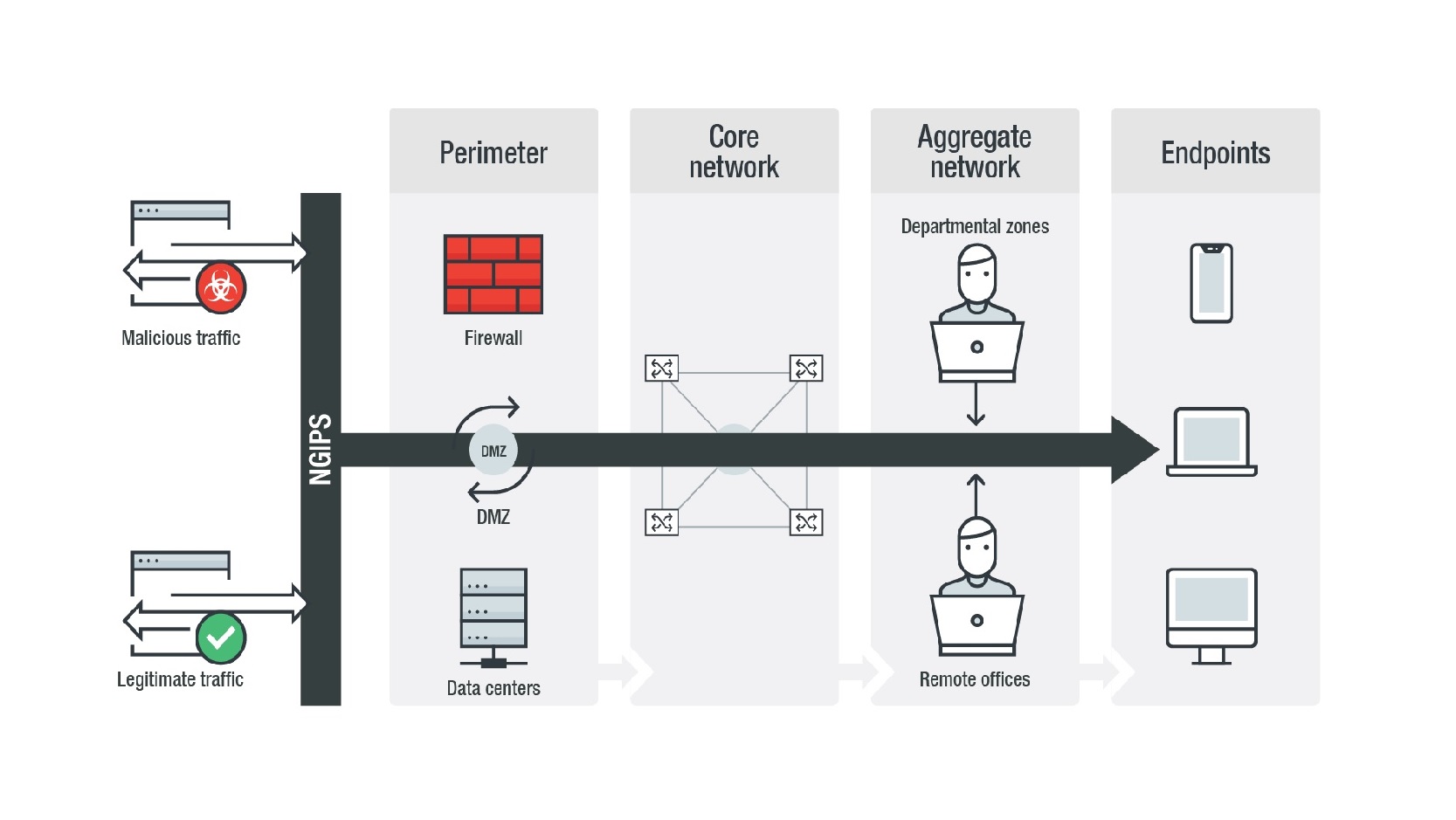

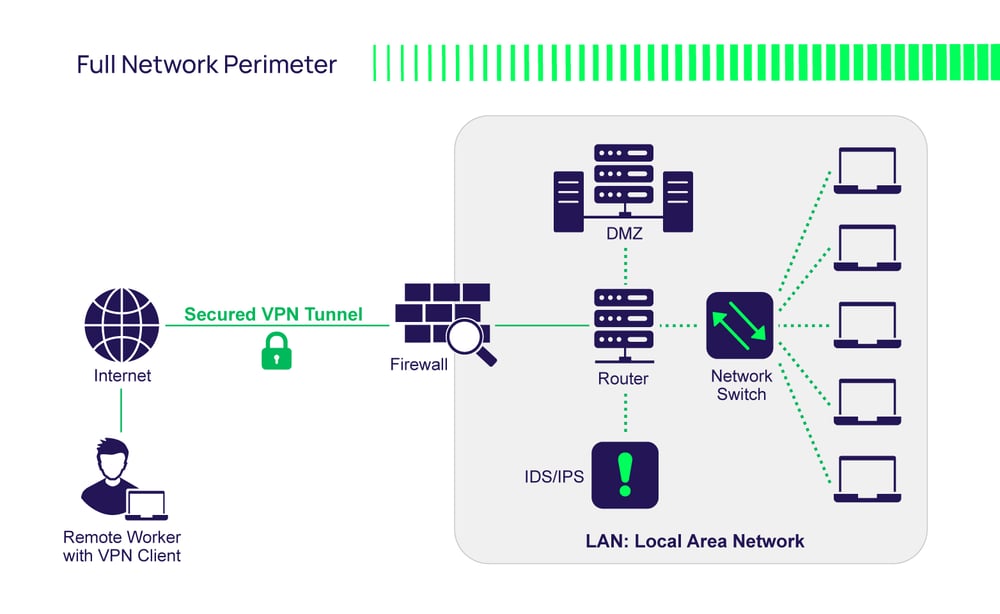
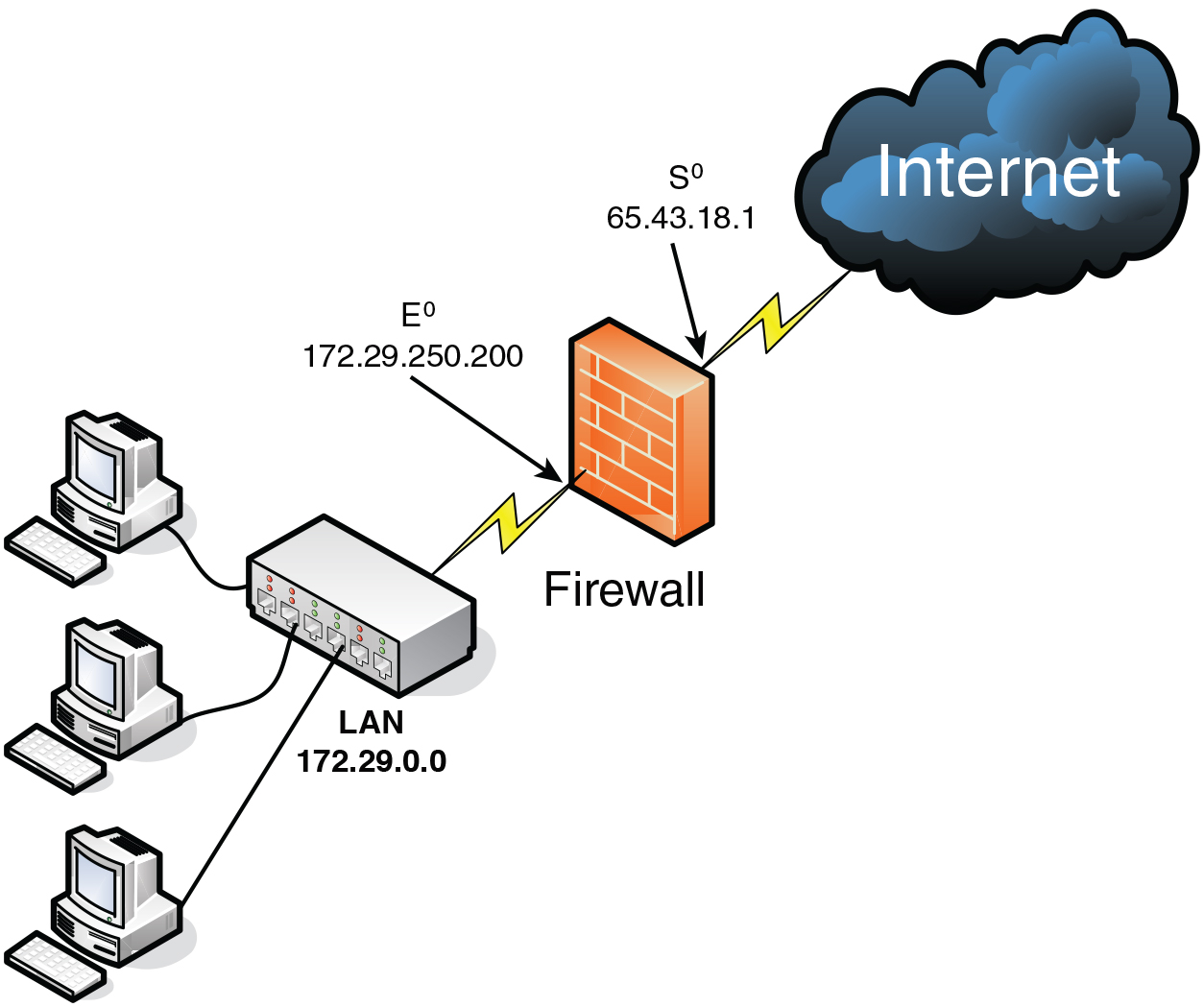
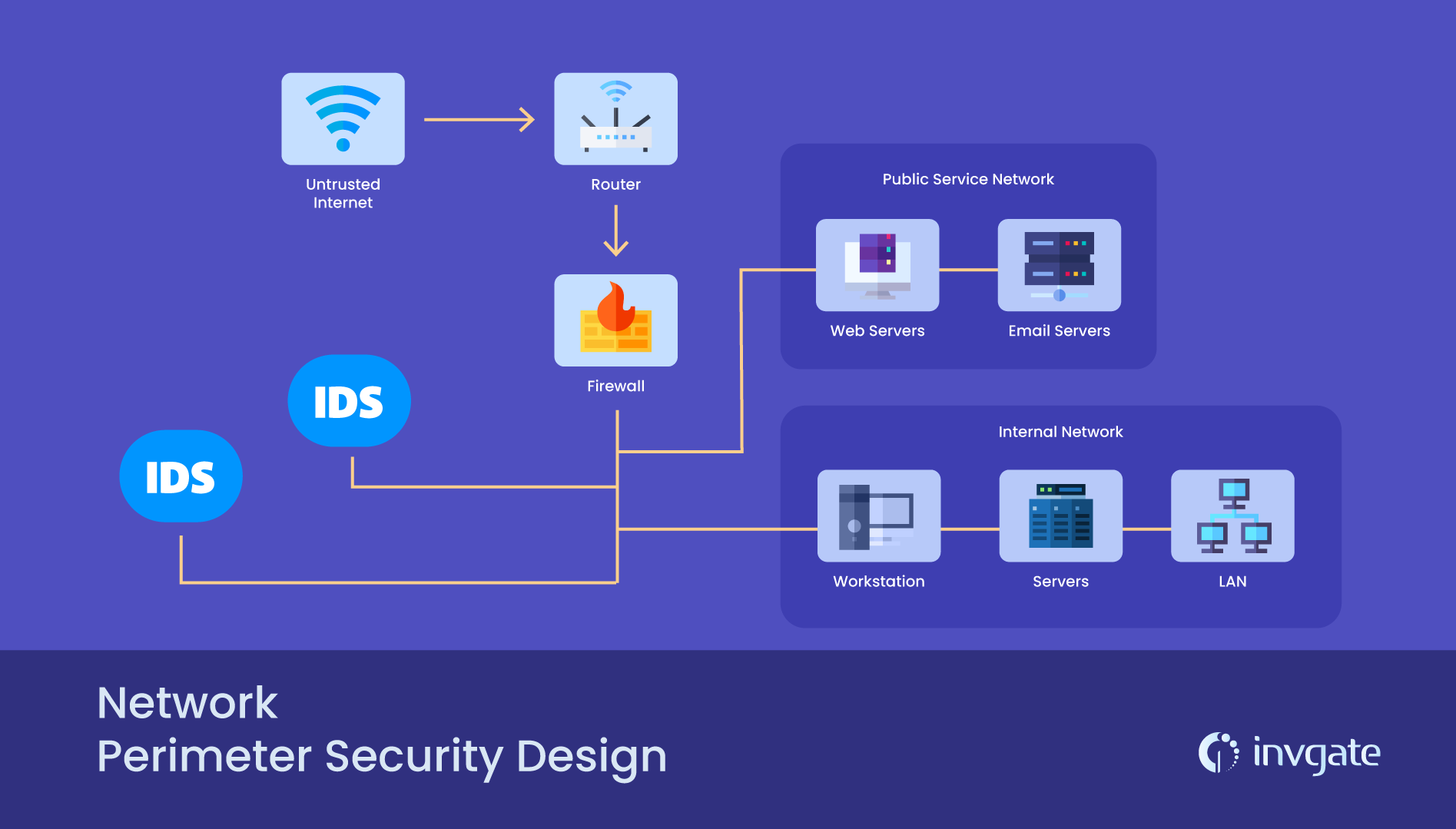


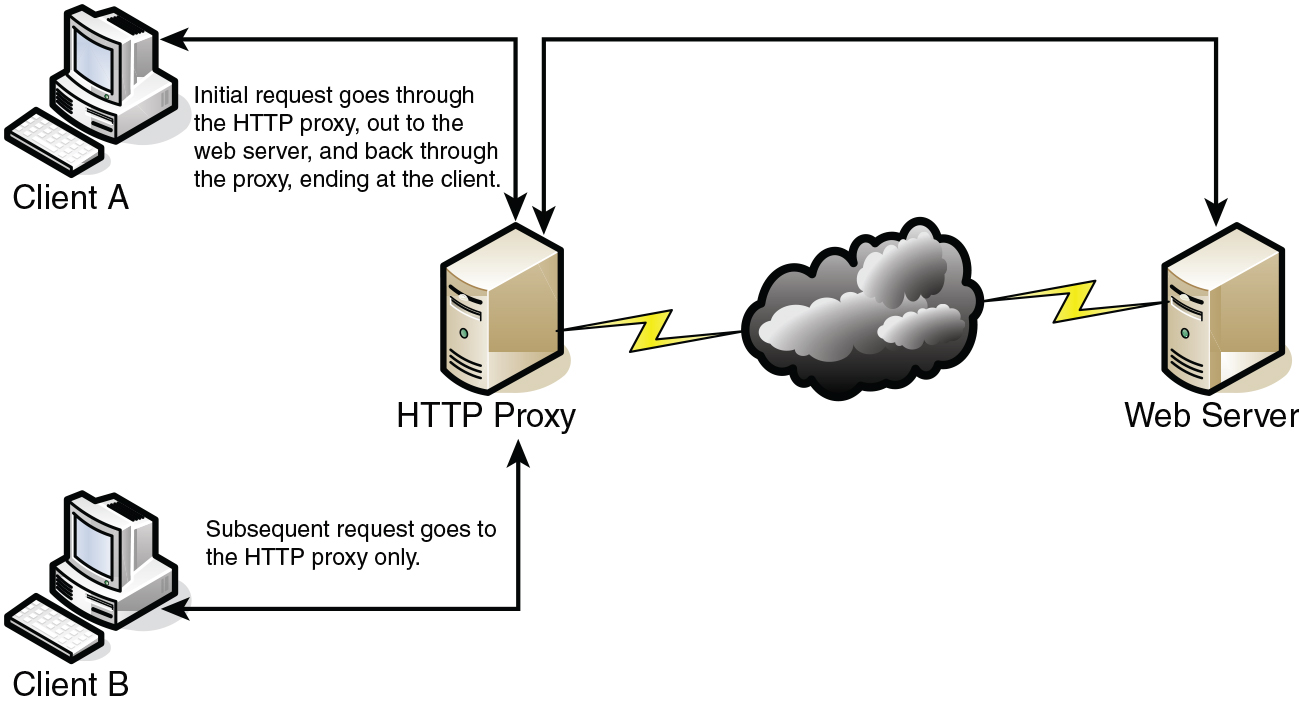


![Introduction [Cisco PIX Firewall Software] - Cisco Systems Introduction [Cisco PIX Firewall Software] - Cisco Systems](https://www.cisco.com/en/US/i/Other/Software/S6001-6500/s6243.jpg)